(me) |
|||
| (25 intermediate revisions by 6 users not shown) | |||
| Line 1: | Line 1: | ||
{{intel title|Management Engine (ME)}} | {{intel title|Management Engine (ME)}} | ||
| − | '''Management Engine''' or '''Manageability Engine''' ('''ME''') is a tiny [[microcontroller]] integrated within all [[Intel]]'s own | + | '''Management Engine''' or '''Manageability Engine''' ('''ME''' or '''IME''') is a tiny [[microcontroller]] [[coprocessor]] integrated within all [[Intel]]'s own chipsets that provide the necessary functionality needed for {{intel|Advanced Management Technology|remote corporate asset management}}, {{intel|Boot Guard}}, {{intel|SGX}} EPID provisioning and attestation services, {{intel|platform trust technology}} (PTT), {{intel|anti-theft}} (AT) technology, and protected audio visual path (PAVP) services. ME was originally introduced into the chipset in [[2006]] and has been present on all Intel mainstream mobile and desktop products ever since. |
| + | == Overview == | ||
| + | Intel's Management Engine (ME or IME) is a [[coprocessor]] implemented as a dedicated [[microcontroller]] embedded into the same [[die]] as the chipset. ME provides all the necessary functionality needed to provide many of Intel's advanced security and many of the [[root of trust]] services. ME was originally integrated into the MCH as bar of Intel's {{intel|965 Express}} chipset which were introduced back in June [[2006]]. Since the 2009, with the introduction of the Core family, ME can be found in all PCHs, meaning it is present on all Intel embedded, mobile, and desktop parts. | ||
| − | {{ | + | == Implementations == |
| + | {| class="wikitable" | ||
| + | ! ME !! Chipset !! Series !! µarch !! Hardware | ||
| + | |- | ||
| + | | 1.x || || || || rowspan="5" | {{arch|32}} [[ARC]] ARCtangent-A4 MCU | ||
| + | |- | ||
| + | | 2.x || || || | ||
| + | |- | ||
| + | | 3.x || || || | ||
| + | |- | ||
| + | | 4.x || || || | ||
| + | |- | ||
| + | | 5.x || || || | ||
| + | |- | ||
| + | | SEC/TXE || colspan="2" | Bay Trail (SoC) || {{intel|Silvermont|l=arch}} || {{arch|32}} [[SPARC]] {{sparc|V8}} MCU | ||
| + | |- | ||
| + | | 6.x || {{intel|Ibex Peak|l=chipset}} || 5 || {{intel|Nehalem|l=arch}} || rowspan="5" | {{arch|32}} [[ARC]] MCU | ||
| + | |- | ||
| + | | 7.x || {{intel|Cougar Point|l=chipset}} || 6 || {{intel|Sandy Bridge|l=arch}} | ||
| + | |- | ||
| + | | 8.x || {{intel|Panther Point|l=chipset}} || 7 || {{intel|Ivy Bridge|l=arch}} | ||
| + | |- | ||
| + | | 9.x || {{intel|Lynx Point|l=chipset}} || 8 || {{intel|Haswell|l=arch}} | ||
| + | |- | ||
| + | | 10.x || {{intel|Wildcat Point|l=chipset}} || 9 || {{intel|Broadwell|l=arch}} | ||
| + | |- | ||
| + | | 11.x || {{intel|Sunrise Point|l=chipset}} || 100 || {{intel|Skylake|l=arch}} || rowspan="6" | {{arch|32}} {{intel|Quark}} [[x86]] MCU | ||
| + | |- | ||
| + | | 11.x || {{intel|Union Point|l=chipset}} || 200 || {{intel|Kaby Lake|l=arch}} | ||
| + | |- | ||
| + | | 12.x || {{intel|Cannon Point|l=chipset}} || 300 || {{intel|Coffee Lake|l=arch}} | ||
| + | |- | ||
| + | | 13.x || {{intel|Ice Lake|l=chipset}} || 495 || {{intel|Ice Lake|l=arch}} | ||
| + | |- | ||
| + | | 14.x || {{intel|Comet Lake|l=chipset}} || 400 || {{intel|Comet Lake|l=arch}} | ||
| + | |- | ||
| + | |} | ||
| + | |||
| + | == Mechanism == | ||
| + | ME is an independent coprocessor, relying on just itself. ME shares the flash with the BIOS, but is otherwise independent. ME can remain active during power off, idle states, and reboots of the main processor. ME has a dedicated connection to the network interface, in theory allowing it to intercept, send, and receive data without the processor's knowledge (or any software/OS knowledge). | ||
| + | |||
| + | === Current Mechanism === | ||
| + | For modern systems, Intel has switched to using their own [[x86]] {{intel|Quark}} microcontroller. | ||
| + | |||
| + | === Historical Mechanism === | ||
| + | [[File:intel management engine.png|right|400px]] | ||
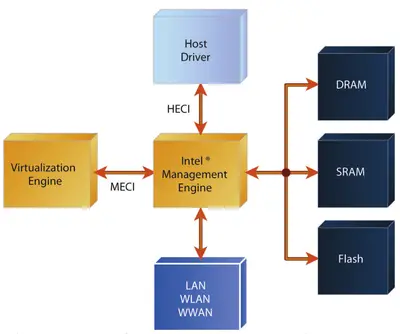
| + | Originally, ME was a {{arch|32}} [[ARCompact]] microcontroller running ThreadX, a [[real-time OS]]. The firmware that was running was developed internally by Intel and provided key management support, access control, and other administrative services. The MCU supported SRAM and DRAM that is isolated from the host processor. Persistent data was stored in flash memory which was accessible by the [[SPI]] bus which stored things such as Intel's AT-d metadata. Data is encrypted in AES-CTR mode using the platform container key (PCK). | ||
| + | |||
| + | ME was connected to both the host driver through an internal bus called the '''Host Embedded Controller Interface''' ('''HECI''') . HECI is bidirectional bus that offers a direct line of communication between the Management Engine and the host OS. ME can also control various aspects of the Virtualization Engine directly over the '''ME Command Interface''' ('''MECI'''). ME also has access to the on-board network interface devices and Intel noted that ME has access to those interfaces even when the system is in [[C-states|low-power states]] and [[Sleep mode]]. Network resources are shared between the ME and the host OS without the host OS ever being aware of this (although Intel stated that some special monitoring tools can be used to detect it). | ||
| + | |||
| + | [[File:intel management engine services.png|450px]] | ||
| + | |||
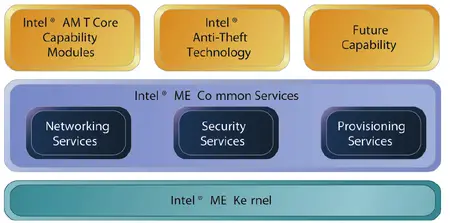
| + | Intel's Management Engine runs modular firmware designed to provide a large number of services. Modules that share a large number of common functions are called ME Common Services (CS) modules. Originally those consisted of three major modules: | ||
| + | |||
| + | * '''Networking Services''' - Full support [[TCP/IP]] stack for both [[IPv4]] and [[IPv6]], [[TLS]], and [[HTTP]]. Support for [[Simple Object Access Protocol]] (SOAP), Web Services for Management (WS-MAN), and a host-based TLS interface called aLocal Manageability Service (LMS) | ||
| + | * '''Security Services''' - Support for secure time, auditing, HTTP digest and Kerberos user authentication, domain authorization (e.g., [[Microsoft]] {{microsoft|Active Directory}}) | ||
| + | |||
| + | * '''Provisioning Services''' - Support for two modes: "Zero Touch", and "One Touch". In zero touch, well-known certificate authority keys can be used to validate IT credentials automagically and take ownership. This is done through firmware-embedded certificate anchor keys for well-known certificate authority. In one touch, organization must configure their own certificates, symmetric keys, and trusted hosts that can then be used to complete deployment remotely. | ||
| + | |||
| + | Note that for the networking services, for IPv4, the host OS shares the same network address with the Intel ME. For IPv6, the Intel ME actually has its own address that is not shared with the host. | ||
| + | |||
| + | == Vulnerabilities == | ||
| + | {{collist | ||
| + | | count = 3 | ||
| + | | | ||
| + | * CVE-2016-8224 | ||
| + | * CVE-2017-5689 | ||
| + | * CVE-2017-5698 | ||
| + | * CVE-2017-5705 | ||
| + | * CVE-2017-5706 | ||
| + | * CVE-2017-5707 | ||
| + | * CVE-2017-5708 | ||
| + | * CVE-2017-5709 | ||
| + | * CVE-2017-5710 | ||
| + | * CVE-2017-5711 | ||
| + | * CVE-2017-5712 | ||
| + | * CVE-2018-3627 | ||
| + | * CVE-2018-3628 | ||
| + | * CVE-2018-3629 | ||
| + | * CVE-2018-3632 | ||
| + | }} | ||
| + | |||
| + | == Secure Coprocessors == | ||
| + | {{secure coprocessor see also}} | ||
| + | |||
| + | == See also == | ||
| + | * {{intel|Innovation Engine}} (IE) | ||
| + | |||
| + | == Bibliography == | ||
| + | * "Storage Protection with Intel® Anti-Theft Technology - Data Protection (Intel® AT-d)", Ned Smith. Intel Technology Journal, Volume 12, Issue 4, 2008. | ||
| + | * REcon 2014, "[https://www.youtube.com/watch?v=4kCICUPc9_8 Intel Management Engine Secrets]", Igor Skochinsky. ([https://recon.cx/2014/slides/Recon%202014%20Skochinsky.pdf Presentation]) | ||
| + | * Libreboot, https://libreboot.org/faq.html#intelme, Frequently Asked Questions | ||
| + | * [https://github.com/corna/me_cleaner me_cleaner] | ||
| + | |||
| + | |||
| + | [[category:intel]] | ||
Latest revision as of 14:55, 15 November 2019
Management Engine or Manageability Engine (ME or IME) is a tiny microcontroller coprocessor integrated within all Intel's own chipsets that provide the necessary functionality needed for remote corporate asset management, Boot Guard, SGX EPID provisioning and attestation services, platform trust technology (PTT), anti-theft (AT) technology, and protected audio visual path (PAVP) services. ME was originally introduced into the chipset in 2006 and has been present on all Intel mainstream mobile and desktop products ever since.
Contents
Overview[edit]
Intel's Management Engine (ME or IME) is a coprocessor implemented as a dedicated microcontroller embedded into the same die as the chipset. ME provides all the necessary functionality needed to provide many of Intel's advanced security and many of the root of trust services. ME was originally integrated into the MCH as bar of Intel's 965 Express chipset which were introduced back in June 2006. Since the 2009, with the introduction of the Core family, ME can be found in all PCHs, meaning it is present on all Intel embedded, mobile, and desktop parts.
Implementations[edit]
| ME | Chipset | Series | µarch | Hardware |
|---|---|---|---|---|
| 1.x | 32-bit ARC ARCtangent-A4 MCU | |||
| 2.x | ||||
| 3.x | ||||
| 4.x | ||||
| 5.x | ||||
| SEC/TXE | Bay Trail (SoC) | Silvermont | 32-bit SPARC V8 MCU | |
| 6.x | Ibex Peak | 5 | Nehalem | 32-bit ARC MCU |
| 7.x | Cougar Point | 6 | Sandy Bridge | |
| 8.x | Panther Point | 7 | Ivy Bridge | |
| 9.x | Lynx Point | 8 | Haswell | |
| 10.x | Wildcat Point | 9 | Broadwell | |
| 11.x | Sunrise Point | 100 | Skylake | 32-bit Quark x86 MCU |
| 11.x | Union Point | 200 | Kaby Lake | |
| 12.x | Cannon Point | 300 | Coffee Lake | |
| 13.x | Ice Lake | 495 | Ice Lake | |
| 14.x | Comet Lake | 400 | Comet Lake | |
Mechanism[edit]
ME is an independent coprocessor, relying on just itself. ME shares the flash with the BIOS, but is otherwise independent. ME can remain active during power off, idle states, and reboots of the main processor. ME has a dedicated connection to the network interface, in theory allowing it to intercept, send, and receive data without the processor's knowledge (or any software/OS knowledge).
Current Mechanism[edit]
For modern systems, Intel has switched to using their own x86 Quark microcontroller.
Historical Mechanism[edit]
Originally, ME was a 32-bit ARCompact microcontroller running ThreadX, a real-time OS. The firmware that was running was developed internally by Intel and provided key management support, access control, and other administrative services. The MCU supported SRAM and DRAM that is isolated from the host processor. Persistent data was stored in flash memory which was accessible by the SPI bus which stored things such as Intel's AT-d metadata. Data is encrypted in AES-CTR mode using the platform container key (PCK).
ME was connected to both the host driver through an internal bus called the Host Embedded Controller Interface (HECI) . HECI is bidirectional bus that offers a direct line of communication between the Management Engine and the host OS. ME can also control various aspects of the Virtualization Engine directly over the ME Command Interface (MECI). ME also has access to the on-board network interface devices and Intel noted that ME has access to those interfaces even when the system is in low-power states and Sleep mode. Network resources are shared between the ME and the host OS without the host OS ever being aware of this (although Intel stated that some special monitoring tools can be used to detect it).
Intel's Management Engine runs modular firmware designed to provide a large number of services. Modules that share a large number of common functions are called ME Common Services (CS) modules. Originally those consisted of three major modules:
- Networking Services - Full support TCP/IP stack for both IPv4 and IPv6, TLS, and HTTP. Support for Simple Object Access Protocol (SOAP), Web Services for Management (WS-MAN), and a host-based TLS interface called aLocal Manageability Service (LMS)
- Security Services - Support for secure time, auditing, HTTP digest and Kerberos user authentication, domain authorization (e.g., Microsoft Active Directory)
- Provisioning Services - Support for two modes: "Zero Touch", and "One Touch". In zero touch, well-known certificate authority keys can be used to validate IT credentials automagically and take ownership. This is done through firmware-embedded certificate anchor keys for well-known certificate authority. In one touch, organization must configure their own certificates, symmetric keys, and trusted hosts that can then be used to complete deployment remotely.
Note that for the networking services, for IPv4, the host OS shares the same network address with the Intel ME. For IPv6, the Intel ME actually has its own address that is not shared with the host.
Vulnerabilities[edit]
- CVE-2016-8224
- CVE-2017-5689
- CVE-2017-5698
- CVE-2017-5705
- CVE-2017-5706
- CVE-2017-5707
- CVE-2017-5708
- CVE-2017-5709
- CVE-2017-5710
- CVE-2017-5711
- CVE-2017-5712
- CVE-2018-3627
- CVE-2018-3628
- CVE-2018-3629
- CVE-2018-3632
Secure Coprocessors[edit]
- Intel: Management Engine (ME)
- AMD: Secure Processor (SP)
- Apple: Secure Enclave Processor (SEP)
See also[edit]
- Innovation Engine (IE)
Bibliography[edit]
- "Storage Protection with Intel® Anti-Theft Technology - Data Protection (Intel® AT-d)", Ned Smith. Intel Technology Journal, Volume 12, Issue 4, 2008.
- REcon 2014, "Intel Management Engine Secrets", Igor Skochinsky. (Presentation)
- Libreboot, https://libreboot.org/faq.html#intelme, Frequently Asked Questions
- me_cleaner