(Spelling correction) |
(grammatical fix) |
||
| Line 17: | Line 17: | ||
=== AArch32/AArch64 Relationship === | === AArch32/AArch64 Relationship === | ||
| − | The changes between the two states can only occur on an exception entry and exception exit. This means it is not possible to branch and link between the two modes of execution and it is not possible to reduce the register width going from one exception to a higher exception level. Those restrictions allow an AAarch32 application to run alongside another AArch64 application under an AArch64 operating system. Additionally, | + | The changes between the two states can only occur on an exception entry and exception exit. This means it is not possible to branch and link between the two modes of execution and it is not possible to reduce the register width going from one exception to a higher exception level. Those restrictions allow an AAarch32 application to run alongside another AArch64 application under an AArch64 operating system. Additionally, they also allow an AAarch32 guest OS to run alongside an AArch32 guest OS under an AAarch64 hypervisor and other similar combinations |
:[[File:armv8 32-64 movement.svg|600px]] | :[[File:armv8 32-64 movement.svg|600px]] | ||
Revision as of 18:08, 2 April 2019
| ARM ISA | |
| General | |
| Variants | |
| Extensions | |
| Topics | |
| Versions(all) | |
ARMv8 is the successor to ARMv7, an ARM instruction set architecture announced in 2011 which brought a large number of fundamental changes to the instruction set, including the introduction of 64-bit operating capabilities.
Contents
Overview
Work on the ARMv8 started within the R&D group at ARM in 2007. First disclosed in late 2011, the ARMv8 is a successor and an extension to the ARMv7 ISA. This architecture introduced new 64-bit operating capabilities, called AArch64, and defined a relationship to the prior 32-bit operating state, referred to as AArch32 (covering the A32 and T32 ISAs). Foundationally, ARMv8 extends the old architecture while maintaining compatibility with older revisions and extensions (e.g., Thumb, NEON, VFP) when in AArch32. Additionally, ARMv8 introduced a number of enhancements to AArch32 which still maintains full compatibility with ARMv7. Generally speaking, ARMv8 was designed such that a well-designed AArch64 core should also work well as an AArch32 core.
AArch32
- Main article: AArch32
ARMv8 introduced the concept of AArch32 execution state to incorporate what was previously ARMv7. It covers the A32 and T32 instruction sets along with a number of new instructions. AArch32 keeps the classical ARM exception model and limits the virtual address to 32 bits.
ARMv8 Enhancements
ARMv8 introduced a set of enhancements to the classic A32 instruction set. The cryptography extensions, enhanced barrier types, and load acquire and store release which were introduced with the A64 were also added to the A32 instruction set.
AArch64
- Main article: AArch64
ARMv8 introduced the new AArch64 execution state that operates on a new instruction set called the A64. This mode reworked the exception handling model in ARM, making it simpler with fewer modes and banked registers. With 64-bit support, up to 48 bits of virtual address was introduced (note that it's actually an extension of the Large Physical Address Extension which was introduced in ARMv7 but was developed concurrently with the ARMv8). Additionally, both security (TrustZone) and virtualization carries over to AArch64.
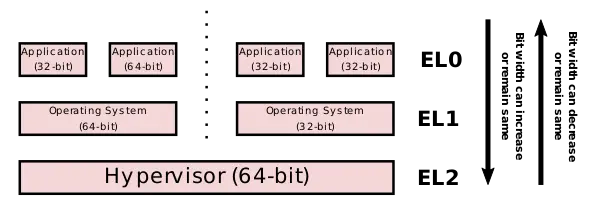
AArch32/AArch64 Relationship
The changes between the two states can only occur on an exception entry and exception exit. This means it is not possible to branch and link between the two modes of execution and it is not possible to reduce the register width going from one exception to a higher exception level. Those restrictions allow an AAarch32 application to run alongside another AArch64 application under an AArch64 operating system. Additionally, they also allow an AAarch32 guest OS to run alongside an AArch32 guest OS under an AAarch64 hypervisor and other similar combinations
Profiles
ARMv8 introduced a number of profiles or flavor of the architecture that targets certain classes of workloads.
| Profile | Name | Description |
|---|---|---|
| Application | ARMv8-A | Optimized for a large class of general applications for mobile, tablets, and servers. |
| Real-Time | ARMv8-R | Optimized for safety-critical environments. |
| Microcontroller | ARMv8-M | Optimized for embedded systems with a highly deterministic operation. |
ARMv8 Extensions and Processor Features
ARMv8 has many versions (ARMv8.1, etc), which define mandatory and optional features. The Linux kernel exposes the presence of some of these features via hwcaps. These values are displayed in /proc/cpuinfo.
| Name | Versions | Feature Supported |
|---|---|---|
| fp | - | Single-precision and double-precision floating point. |
| asimd | - | Advanced SIMD. |
| evtstrm | N/A | Generic timer is configured to generate "events" at frequency of about 100KHz. |
| aes | - | AES instructions (AESE, etc) |
| pmull | - | Polynomial Multiply Long instructions (PMULL/PMULL2) |
| sha1 | - | SHA-1 instructions (SHA1C, etc) |
| sha2 | - | SHA-2 instructions (SHA256H, etc) |
| crc32 | [ARMv8.0], ARMv8.1 ... | CRC32/CRC32C instructions |
| atomics | ARMv8.1 ... | Large System Extensions (LSE) - (CAS/SWP/LD[op]) |
| fphp | ARMv8.2-FP16 | Half-precision floating point. |
| cpuid | N/A | Some CPU ID registers readable at user-level. |
| asimdrdm | ARMv8.1 | Rounding Double Multiply Accumulate/Subtract (SQRDMLAH/SQRDMLSH) |
| jscvt | ARMv8.3 | Javascript-style double->int convert (FJCVTZS) |
| lrcpc | ARMv8.3 | Weaker release consistency (LDAPR, etc) |
| dcpop | ARMv8.2 | Data cache clean to Point of Persistence (DC CVAP) |
| sha3 | ARMv8.2-SHA | SHA-3 instructions (EOR3, RAXI, XAR, BCAX) |
| sm3 | ARMv8.2-SM | SM3 instructions |
| sm4 | ARMv8.2-SM | SM4 instructions |
| asimddp | ARMv8.2-DotProd | SIMD Dot Product |
| sha512 | ARMv8.2-SHA | SHA512 instructions |
| sve | ARMv8.2-SVE | Scalable Vector Extension (SVE) |
Crypto Extension
ARMv8 introduced hardware acceleration for cryptography. Those operations were added to complement, but not replace, traditional crypto accelerators. Geared for small instruction-level crypto support, two main algorithms were supported: AES and SHA (SHA-1 and SHA-256).
Bibliography
- Richard Grisenthwaite. (October 26, 2011). "Technology Preview: The ARM Architecture - a View of the Future ".
- ARM Architecture Group. "Armv8 instruction set overview." vol. PRD03-GENC-010197 (2011).
- elf_hwcaps.txt